Zero trust (ZT) is an evolving cybersecurity model featuring a set of concepts that will guide government agencies and enterprise IT providers toward both the solutions and the constant vigilance required to counter the evolving tactics of today’s cyber adversaries.
With direction being provided by the Cybersecurity and Infrastructure Security Agency (CISA), the National Institute of Standards and Technology (NIST), and the Office of Management and Budget (OMB), ZT is currently evolving from industry buzzword to government mandate, driving new policies and processes based on a simple principle: “Never trust, always verify.”
A ZT approach addresses the archaic constructs and limitations of traditional networks, shifting from a reliance on static, location-centric security perimeters that grant users implicit rights, toward a more dynamic model predicated on trust-zones, data segmentation, and explicit relationships.
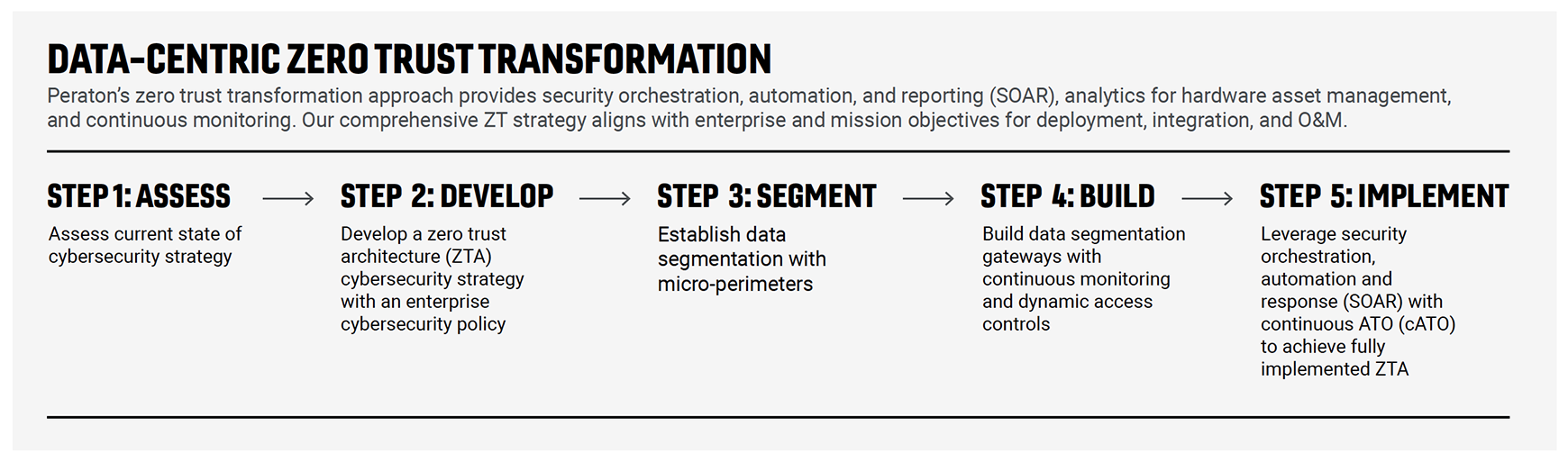
There’s no single, simple solution—it’s not all or nothing—and ZT is perhaps best understood as a journey or a new mindset. Peraton is currently guiding a number of federal agencies on that journey, assessing, developing, and deploying custom solutions that fit their unique information security needs.
Peraton’s Approach
There are numerous ways to design and implement a zero trust solution that fulfills government requirements and positions an organization for a successful digital transformation with a robust cybersecurity posture.
The key to translating ZT concepts into successfully implemented solutions is to understand the agency customer—both its unique technical and business challenges and its place in the evolving cyber threat environment—and then selecting and integrating the systems and tools that best meet that agency’s specific technology requirements.
As a leading mission capability integrator and transformative enterprise IT provider, Peraton is committed to finding the best ZT solutions for each of its government customers and is uniquely positioned to offer best-in-class customized offerings.
Here are several case studies where Peraton guided federal agencies to successful zero trust transformations:
Case Study 1:
Federal Defense Agency
The Challenge: Outdated Cybersecurity Posture
A federal defense agency’s networks were vulnerable to sophisticated cyber threats, protected only by anti-virus software and large external firewalls. These networks were password-protected and only passively monitored; the agency was not employing micro-perimeters or using internal data segmentation.
Cyber incident data was captured electronically in data logs and batch processed for data analysis, using a basic intrusion detection system (IDS) at key monitoring points enterprise-wide. Later, the information security analyst would study the cyber data logs and related data analysis to determine if a cyber incident ticket was needed.
Unfortunately, this method of passive/reactive monitoring:
- Did not notify security analysts of abnormal user behavior or an active cyberattack
- Did not block or mitigate cyberattacks
- Did not facilitate timely cyberattack remediation.
The Zero Trust Solution
Peraton developed a customized solution that would enable the defense agency to shift from a passive/reactive cybersecurity posture to a proactive zero trust architecture (ZTA) approach.
The Peraton solution featured a combination of systems and tools that could deploy micro-perimeters to monitor internal network traffic while leveraging an extended endpoint detection and response system that could be fully integrated with advanced data analytics using security orchestration and automated response (SOAR) technology.
The Result
Now fully authorized and approved, the Peraton-designed ZTA solution has been successfully implemented, and traffic inside the agency’s network is currently monitored by next-generation firewalls, protecting more than 1,000 users.
This solution provides advanced, proactive security from device to device—adding a micro-perimeter for each site, providing access control, and proactively managing information flow—while integrating SOAR technology to provide automated incident response playbooks for rapid cyberattack remediation.
Case Study 2:
Federal Civil Executive Branch Agency
The Challenge: A New Approach to Trusted Internet Connection 2.0
A large FCEB agency was searching for a new approach to the Trusted Internet Connection (TIC) 2.0 program by implementing a ZTA solution. Peraton initiated an Independent Research and Development (IRAD) project to determine the best approach to designing and integrating a ZTA.
The Zero Trust Solution
Working with a technology partner, Peraton designed a ZTA solution using a secure access service edge (SASE) approach, which securely connects users to managed software applications, internally and externally, including both software-as-a-service (SaaS) and internet destinations, regardless of device, location, or network.
This cloud-based architecture is built upon a FedRAMP-certified infrastructure.
The Result
Peraton tested the ZTA solution as a proof-of-concept and was able to inspect all information system traffic, including encrypted traffic, and enforce security policy for identity, access, and control—dynamically, with continuous monitoring and analysis.
For government agencies looking to modernize and improve cybersecurity while supporting cloud adoption and a remote/mobile workforce, this proved to be an elegant, scalable solution—and one that Peraton has since incorporated into eight unique agency proposals.
Read a third case study and learn more about Peraton’s technical approach to ZT.