The Problem Peraton’s Solution The Value Delivered
The Problem
A United States government agency made the decision to decommission its mainframe case management system and umbrella applications with an aggressive deadline of under 12 months—requiring an accelerated timeline to meet the target.
The agency needed a scalable and sustainable software architecture to support the mission-critical applications that could be easily integrated with other enterprise applications and support critical data exchange with other federal agencies.
Peraton’s Solution
The existing case management mainframe system hosted legacy applications and associated data that required decommissioning. To improve agility, security, and sustainability, the Peraton team created a roadmap after assessing application capabilities, the agency’s mission, and business and technology strategies.
Peraton recommended a three-part solution to migrate the features and functionality off the mainframe:
- Obtain a complete understanding of the business requirements
- Re-architect the application and database to a sustainable, modern framework
- Implement the architecture using DevSecOps best practices for flexibility and agility
The Peraton team made a collaborative effort to extract and define current business needs for these applications using the COBOL source code. The Peraton team, comprised of business analysts and legacy mainframe developers, analyzed the COBOL source code to draft initial sets of feature level user stories.
The team then worked closely with their government counterparts, business product owners, and interfacing partner agencies to validate the user stories and acceptance criteria.
With a full understanding of the legacy applications, Peraton leveraged enterprise grade software tools to develop the interface application using cloud native technologies.
We adopted a DevSecOps methodology and built an automated pipeline, which extracted code directly from the source and compiled, tested and scanned the code before deploying the applications. This enabled seamless execution of a continuous integration/continuous deployment (CI/CD) process.
We ensured compliance with government mandated security practices by allowing for continuous feedback of security status and the prompt mitigation of potential vulnerabilities. The Peraton team configured the pipeline tools as depicted in Figure 1 below.
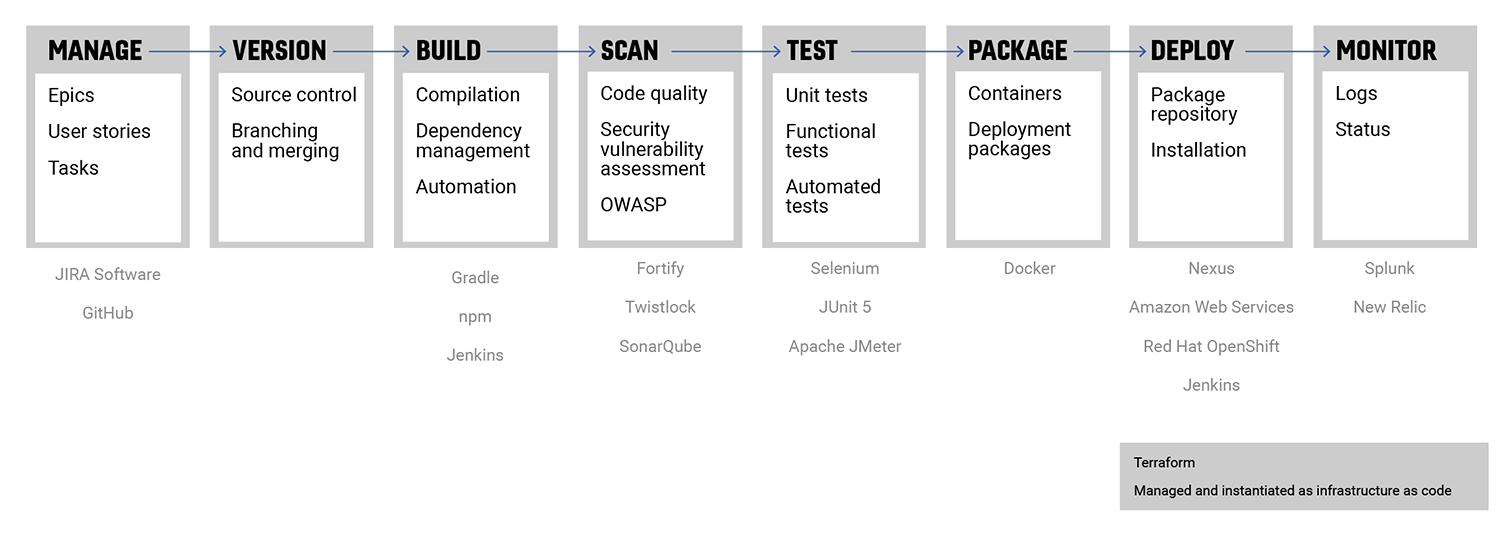
Figure 1: Case Management Solution
Amazon Web Services (AWS) Integration
The Peraton team leveraged AWS tools1 and services to design and deliver the solution. Peraton proposed that the agency’s data exchange interfaces be reengineered as microservices, with a cloud native architecture using a twelve-factor application2 methodology.
Following cloud-first principles, the services were designed to be scalable, fault tolerant, and self-healing. This was achieved through containerization and deployment to the AWS Cloud. All infrastructure was managed as code in accordance with infrastructure as code (IaC) standards.
Containers were architected using best practices from the Center for Internet Security3 and guidelines from the agency.
The Value Delivered
The Peraton team was successful in completing the agency’s mainframe decommissioning objective within the mandated timeline, meeting customer expectations.
Migration to the AWS Cloud and adopting a cloud-native microservices architecture helped enhance customer experience, reduce application downtime, and improve performance. Adoption of DevSecOps practices provided the qualitative benefits of agility and scalability.
- Simple Queue Service, Relational Database Service, Identity and Access Management, Simple Storage Service, CloudWatch, and Simple Notification Service in addition to the other platform services, such as the RedHat OpenShift Container Platform.
- Twelve-factor application methodology is used to build software as-a-service applications.
- The Center for Internet Security provides global industry standards for cybersecurity.
Published: Jul 17, 2023